Imagine, you have a mobile phone that you use for work. And you have stored banking information, client’s details, login information for services that you subscribed and lots of registered data pertaining to the private workings of your business. There is a chance that your mobile phone might be lost or stolen at some point. If that situation occurs, what happens to the data saved on your device? How do you defend your own privacy and information security? What about safeguarding the information of your clients?
The answer to all of these questions is to create
an Information Security Management System (ISMS)—a set of policies,
procedures, and protocols intended to protect sensitive data at your business
and prevent it from either being wrecked or dropping into the wrong hands.
Erudite technologies are capable of
combating cybersecurity attacks, but these are not sufficient:
organizations should ensure that policies, business processes and workforce
performance mitigate these cybersecurity risks. However, this path is neither
easy nor clear, companies approve frameworks that give assistance towards
information security best practices. This is the reason why information
security management systems (ISMS) come into picture.
An ISMS characteristically reports employee behavior and
processes as well as technology and data. It can be battered towards a data,
such as customer data, or it can be instigated in a inclusive way which becomes
part of the company's ethos.
What is an Information Security Management System (ISMS)?
An information security management system (ISMS) is a
framework of policies and procedures for methodically managing an
organizations’ sensitive data. The goal line of an ISMS is to minimalize
risk and safeguard business continuity by pro-actively limiting the effect
of a security breach. These security controls can follow common security standards
or be more focused on your industry. The framework for ISMS is usually focused
on risk assessment and risk management.
For example, ISO 27001 is a set of provisions
specifying how to implement, manage and create ISMS policies and controls. The
ISO does not command specific actions but includes proposals for documentation,
internal audits, constant improvement, and corrective and defensive action.
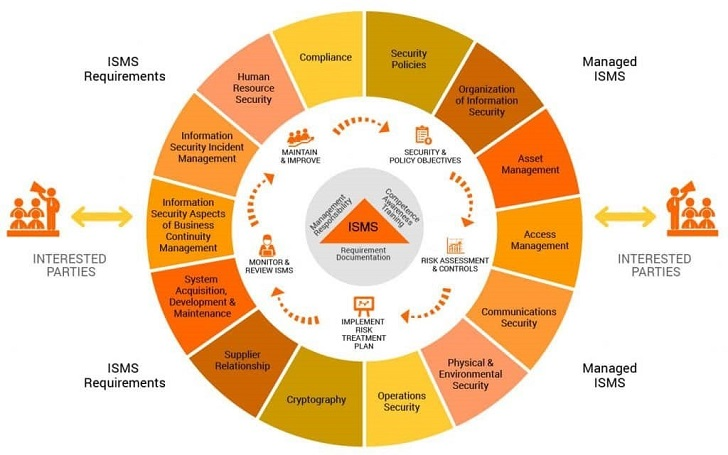
ISMS security controls
ISMS security controls extent multiple fields of information
security as stated in the ISO 27001 standard.
The catalog contains practical guidelines with the following
objectives:
Information security policies: An overall
direction and support help to establish suitable security policies. The
security policy is exceptional to your company, planned in context of your
changing business and security needs.
Organization of information security: This
addresses threats and risks within the corporate network, including
cyberattacks from external entities, inside threats, system faults, and data
loss.
Asset management: This component covers
organizational assets within and outside the corporate IT network, which may
involve the exchange of sensitive business information.
Access control: This policy domain deals with
preventive access to authorized personnel and monitoring network traffic for
irregular behavior. The roles and responsibilities of folks should be well
defined, with admittance to business information available only when necessary.
Communications and operations management: Systems
must be functioned with esteem and care to security policies and controls.
Daily IT operations, such as service and problem management, should trail IT
security policies and ISMS controls.
Physical and environmental security: These
guidelines cover security actions to protect physical IT hardware from damage,
loss, or unauthorized access. While many organizations are taking advantage of
digital transformation and maintaining sensitive data in secure cloud networks
off-premise, security of physical devices used to access that information must
be measured.
Cryptography: ISMS administer how cryptographic
controls are required and accomplished.
Supplier relationships: Third-party vendors and
business partners may need access to the network and sensitive customer data.
It may not be possible to enforce security controls on some suppliers. However,
adequate controls should be adopted to mitigate potential risks through IT
security policies and contractual obligations.
Information system acquisition, development, and
maintenance: Security best practices should be maintained across the
entire lifecycle of the IT system, including the phases of acquisition,
development, and maintenance.
Information security and incident management: Identify
and resolve IT issues in ways that minimize the impact to end users. In complex
network infrastructure environments, advanced technology solutions may be
required to identify insightful incident metrics and proactively mitigate
potential issues.
Business continuity management: Avoid
interruptions to business processes whenever possible. Ideally, any disaster
situation is followed immediately by recovery and procedures to minimize
damage.
Compliance: Security requirements must be
enforced per regulatory bodies.
These components and areas offer general best practices
towards ISMS success.
How to Implement ISMS at Your Organization
Organizations can take advantage from implementing an ISMS,
accomplishing compliance with ISO 27001, and safeguarding the security of their
informational assets, but a thorough execution and training process is required
to originate the complete benefits of the ISMS. Here I am demonstrating 3 steps
procedures to start implementing ISMS at your organization:
Step One: Asset Identification and Valuation
The first step to implementing an ISMS is to recognize the
assets that must be protected and govern their relative value to the
organization. In this step, organizations collect data from documentation to
recognize business-critical IT assets and their relative importance to the
organization.
Organizations must create a Statement of Sensitivity (SoS)
that allocates a rating to IT assets across three separate dimensions—
availability, confidentiality and integrity:
Availability- Ensures that authorized person has
access to the protected data and assets when needed.
Confidentiality- Ensures that the data is entirely
available to authorized persons only.
Integrity- Ensuring that the data to be secured
is accurate and complete, and that data and processing methods are secured.
Organizations must strike a stability between securing
assets and making them accessible to authorized persons that may need the data
to do their jobs.
Step Two: Conduct a Detailed Risk Assessment
Once asset identification and valuation have been completed,
it is time to conduct a detailed risk assessment that will notify the
production of the ISMS. A risk assessment analysis contains four important
steps for defining how the IT asset should be threatened:
Threats- The organization should analyze the
threats to the asset by documenting any unwanted events that could result in
accidental misuse, loss, or damage of the assets.
Vulnerabilities- Threats are a tangible
description of what could occur, and vulnerabilities are a measure of how
susceptible the IT asset could be to the threats identified in the first part
of the analysis.
Impact and Likelihood- The organization can now
measure the likelihood of certain types of breaches occurring along with the
magnitude of the possible damage that would result from each type of data
breach.
Mitigation- Lastly, the organization suggests
methods for minimizing the familiar threats, vulnerabilities, and impacts
through policies and procedures in the ISMS.
Step Three: Establish the ISMS
Now the organization has identified the assets to be
protected and conducted a full risk assessment, it can proceed to write the
actual policies and procedures that include ISMS.
Going back to our first example of the unsecured business
phone, what steps could the organization take to safeguard that information on
the phone is sufficiently protected in case the phone is lost or stolen? Here
are some model policies that could be applied to support mitigate the risk:
- Lost
or stolen phones must be reported to the IT department within eight hours.
- IT
must have the ability to remotely track and wipe any phone owned by the
company.
- Company
phones must be protected by a biological password that matches to the
assignee—a fingerprint or facial recognition technology must be used to
unlock the phone.
- Company
phones are issued with a secure waist holster, encouraging employees to
avoid losing the asset by securing it to their person when not in use.
These set of policies and procedures would minimize the
possibility of a data breach occurring due to a lost phone. The requirement of
a biological password significantly increases the level of complexity required
to gain unauthorized access to the phone, the reporting requirements introduce
additional accountability to the user of the phone, and IT is able to remove
sensitive data from any phone that is reported missing.
Summary
An ISMS is a set of policies and procedures that establish how your company will protect its information assets from cautious or accidental misuse, loss, or damage. Establishing an ISMS is an important step towards securing your organization's data assets and protecting yourself from the legal and financial implications of a data breach. Organizations can gain ISO 27001 certification by complying with the global standards for ISMS. Implementation of ISMS requires organizations to identify and evaluate their assets, conduct a risk assessment, and document the established policies and procedures. Training programs are required to ensure that employees are compliant with the ISMS when handling sensitive data.